talks
traditionally talking in the library is illegal but somehow these people are getting away with it
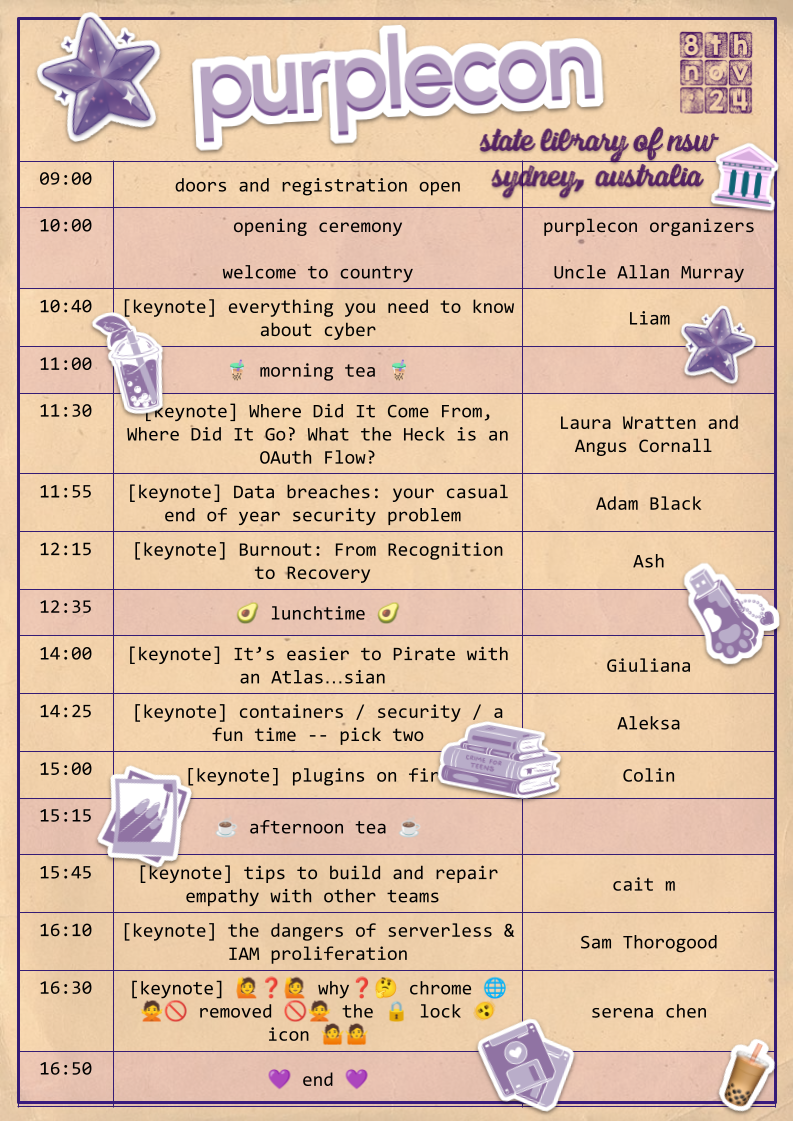
[keynote] everything you need to know about cyber
it is simply not possible to learn everything you need to know about cybersecurity in a 20 minute talk slot, but we're going to do it anyway
Liam
Liam started his career in cyber so long ago that it was still called infosec. He worked for many years as a software engineer before discovering that breaking things could be more fun than building things and jumped the fence to offensive security. He has worked as a pentester for over 10 years. Liam is enthusiastic about ducks
great archive submission
purplecon-2024-liam-everything-cyber.pdf
[keynote] Where Did It Come From, Where Did It Go? What the Heck is an OAuth Flow?
OAuth can feel like a big, scary monster full of techy jargon and tricky standards. But it doesn't have to be that way! Ever clicked "Connect with Apple" or allowed an app to access your calendar? That’s OAuth in action! Join us for a friendly and easy-to-understand exploration of OAuth, specially crafted for beginners.
In this talk, we'll break down the most important bits from the official documents (RFCs) and take you on a quick tour through OAuth history—from OAuth1 to current best practices. We'll delve into what OAuth is, how it works, and why it has evolved over the years.
Laura Wratten and Angus Cornall
Laura and Angus are best friends, and Application Security Engineers at Canva. Laura is passionate about good security education and wholesome security vibes (oh, and permaculture, fermenting, and rescue greyhounds). Angus loves diving into hands-on security and helping others do the same, as well as hiking, biking and traveling. Both have mildly cursed vocabularies from years of memes that turned from ironic to regular speech 😂.
great archive submission
[keynote] Data breaches: your casual end of year security problem
This talk is aimed at those new to security. Every year (financial year) organisations send out tax summaries. Undesirably some of these are vulnerable to Insecure Direct Object Reference. This talks provides an intro to this area of security and how to avoid it
Adam Black
A software engineer with a passion for security
great archive submission
[keynote] Burnout: From Recognition to Recovery
Have you been feeling more stressed and exhausted lately? You're not alone.
Feeling burnout is a sign that something needs to change. This talk explores the common burnout causes and symptoms, and discusses practical strategies for recovery.
Ash
Ash is an engineer working in incident response and product security. They are passionate about creating an inclusive and supportive tech community where everyone can thrive. Between responding to security incidents and advocating for secure coding, they can be found climbing mountains, and teaching computer science to school students.
great archive submission
[keynote] It’s easier to Pirate with an Atlas…sian
Have you ever wondered exactly how people pirate software? What are the tools and techniques they used? At Atlassian, every new penetration tester writes a crack for Jira during their first couple of weeks. Why? Because those same tools and techniques used to pirate software are critical skills needed to perform effective security tests & research. In this talk, I’m going to teach some of those techniques to you too! We’ll dive into Jira DC together with a hacker mindset, reverse engineering the logic behind its license check and exploring how we can modify and debug it.
Giuliana
Hi! I’m Giuliana, a Security Testing engineer at Atlassian (or pentester, cartoon character, or whatever else suits you). Aside from poking at things on my laptop until it does something it’s not supposed to, I like everything fashion, food and friends, so come say hi!
great archive submission
[keynote] containers / security / a fun time -- pick two
containers might be old news, but securing them sure as heck 'aint! it turns out we are still battling with age-old Unix problems with healthy helping of slightly-less-old Linux problems that have been maturing in oak casks with labels that just read "beware of the leopard". paths? procfs? persistently pesky pernicious problems? oh my! hold on to your hat and join me on a whirlwind tour of this lovely little tyre fire! was "/" a mistake? tune in to find out!
Aleksa
Aleksa has worked on container technologies for the past decade (yikes, has it really been that long?! 😬), maintaining the most commonly used Linux container runtime (runc) and Open Container Initiative specifications. He also does a fair amount of Linux kernel work for quite a few years, mostly focusing on trying to modernise kernel APIs to allow for more secure systems software on Linux.
[keynote] plugins on fire
If you're new to security code review or bug bounties, finding vulnerabilities in WordPress plugins could be a gentle entrypoint that allows you to learn by doing, while racking up CVEs and a bit of money along the way - not to mention you'll be improving the security of thousands (or even millions!) of sites that rely on these plugins.
Come along to find out more about how you can get started (or just come for the memes, you do you). This is not a hardcore hacking talk, but there will be recommended resources for you to dive as deep as you want for homework
Colin
𓁹‿𓁹 heh
great archive submission
https://hackmd.io/@3TuSi7xDS-GMp7ZFbJPcoA/Bk_W2Pnbye
[keynote] tips to build and repair empathy with other teams
Everything works better if the teams involved work together instead of against each other. But many teams I've worked in have had longstanding issues, misunderstandings or grudges, which caused stress and poorer work outcomes for all involved.
We'll talk through some tips, resources and mindsets I've found useful when working on repairing team relationships, both as a newcomer and when trying to reset my own mindset.
cait m
cait lives in Naarm Melbourne with their cat Mickey and works as a consultant with Red Hat. they do Linux and security stuff, and try to empathise and enable teams to improve their culture and impact.
great archive submission
talk - tips to build and repair empathy with other teams - purplecon.pdf
[keynote] the dangers of serverless & IAM proliferation
grug dislikes complex software (and security model) which is like ball with million spikes, makes grug brain sore just by holding. instead grug thinks treat whole ball like sandpaper, all together low-level spiky. grug will permit small number of big spikes because easier to understand where actual risky bits are, like bear cave over there.
Sam Thorogood
I have opinions™
great archive submission
[keynote] 🙋❓🙋 why❓🤔 chrome 🌐 🙅🚫 removed 🚫🙅 the 🔒 lock 🫨 icon 🤷🤷
if you've been particularly eagle-eyed, you might've noticed that within the past year or so, the lock icon disappeared from Chrome's address bar. this is the story of why and how that happened, and maybe it's secretly a story about HTTPS and the web ecosystem and the sisyphean task of securing the web as a whole......
it's just an icon, michael. how hard could it be to remove?
serena chen
serena is an ex-physicist and mathematician, once teen magazine editor-in-chief, foosball enthusiast and hacker at heart. for her day job she's cyber aesthetics doctor at google chrome, leading UX for chrome security.
great archive submission
💜 why chrome removed the lock icon 💜 purplecon sydney 2024 💜.pdf